Introduction
EuroCloud was the first organization to offer cloud service certification in Europe, under the name of the EuroCloud Star Audit. This certification is specifically designed for IaaS, PaaS and SaaS and defines graded levels of performance to be met in specific fields if the cloud service provider in question is to be certified as reliable.
Far-reaching expertise is required for the qualitative testing of the performance in the fields of data security, technical operation and organizational processes needed to confirm that the service provision meets the requirements laid down in the warranty. For this reason, quality certificates generally make concise statements on the security performance and reliability of the service provider.
EuroCloud has designed a special seal of approval showing that contractual, technical and organizational requirements have been met. This approval can only be used by cloud service providers whose performance has been thoroughly tested by qualified auditors and who have received a certificate confirming that they achieved the stipulated standards.
Compliance
Many cloud services are currently marketed under brand names or offered via portals that mask the identity of the provider. In such cases, it is advisable to determine who the actual service provider is.
General compliance requirements
Compliance in general means that a company’s operations must meet all relevant requirements of correctness, probity and integrity. In the field of cloud computing, compliance of the service provider can only be ensured through adequate transparency of all matters concerning service provision, including the actual location of the data, full details of the service provider and the functions offered, and the assurance that the contract provides all necessary service guarantees. In addition, the provider must notify the user of any changes to be made in the services provided. If changes are made the user must have the opportunity to terminate the contract if he does not accept these changes. In this case provisions must be made for the data to be returned to the user in a proper form
On Site visit
The need to check the performance of external IT providers in the field of cloud computing is likely to lead to increasing problems in the future. Many data protection regulations require on-site testing of service providers. However, the question then arises, which “site” is intended here: the location of the party who signs the contract, of the computer centre manager or of the software operator? If it is decided that the relevant location is that of the data, it must then be asked what information one can expect to derive from a personal visit to the computer centre?
Without extensive testing by qualified experts in the field of data protection, data security, operational management and possibly also software development, the most that can be expected is a subjective impression of whether the party in question seems to be reliable which will not even include qualitative assessments of the technical and organizational measures taken. It should be added, in this connection, that a visit to a computer centre represents a security risk in itself, and only qualified persons, who would furthermore have to undergo appropriate security and access checks would be permitted.
A combination of IT services (self-operated, private IT outsourcing, private cloud and public cloud), to which extra basic services such as identity management and data interface management should be added, needs to be taken into consideration. It should furthermore be noted that most public cloud services are structured as a supply chain, in which a whole series of links (computer centre, IaaS provider, platform operator, SaaS provider and marketplace provider) work together to provide the actual service.
The only way to get out of this labyrinth is to make use of certification by recognised test institutes, which are playing an increasingly important role in demonstrating the quality of products and services in this and other fields.
Skills
The thorough testing of all relevant functions must be based on wide-ranging professional skills and experience. That is why certification by recognised test institutes is required to demonstrate the quality of cloud computing services.
This quality is checked first of all with reference to the technical requirements, and then in respect of the more general requirements of security, data protection, compatibility and compliance. Such an audit must be based on criteria and test requirements that extend beyond purely technical considerations. The fact that such audits are generally extensive and time-consuming, and require special test expertise, has led to the development of certification procedures.
This involves setting general requirements in the framework of a standardized test protocol, which is performed by qualified auditors. ISO standard 27001 (Information technology – Security techniques – Information security management systems – Requirements) gives details of the best-known test procedure in the field of IT security.
However, security is just one of the aspects that have to be tested in the field of cloud computing. The specification of service level agreements (SLAs) and the contractual formulation of data protection requirements are also highly relevant in this connection. Since cloud services are often provided to a number of users, there is also a need to test whether the requirements are met throughout the supply chain.
Even if a SaaS solution provider has ISO-27001 certification, this tells us nothing about the security systems used by providers earlier in the supply chain, such as embedded platform or infrastructure providers.
Requirements
The audit covers certain legal aspects, the reliable performance of technical services such as data protection, data security and the attainment of basic quality standards for operating processes and applications. The service provider must furnish concrete evidence for information he provides for the purposes of the audit, and must also undertake to report significant changes in the terms of the service provision (such as the location of the activities involved and changes in subcontracting agreements) and to give immediate notification of critical incidents.
What needs to be addressed?
- Cloud Specific Assessment
- Security Assessment
- Legal Compliance Assessment
- Data Privacy Assessment
- Common Scope - no negotiations
- Complete Cloud Supply Chain covered
- publicly available Controls
Comparison of certification schemes:

Study of the University of Cologne: CLOUD SERVICE CERTIFICATIONS: MEASURING CONSUMERS’ PREFERENCES FOR ASSURANCES
Authors: Lansing Jens, Schneider Stephan; Sunyaev Ali
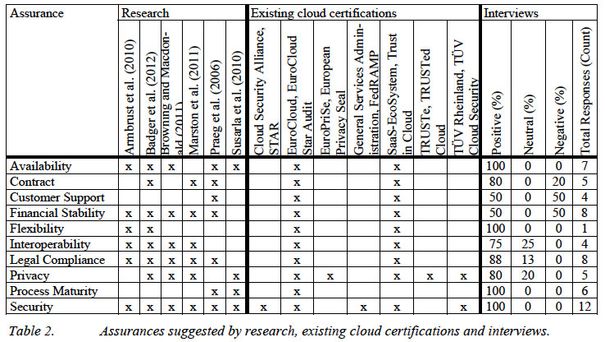
Table 2 provides an overview of the ten identified assurances and their corresponding representation in research, existing cloud certifications and interviews. Existing certifications vary, among other aspects, by provided assurances. Most current cloud service certifications focus on security and privacy, which is in line with major concerns of (potential) cloud users. However, our results indicate that security and privacy are not the only assurances that need to be provided by effective certifications.
Catalogue
A list of test requirements has been drawn up in close consultation with official bodies, research institutes, legal experts and accountancy firms.
The evaluation of a Cloud Service is carried out on the basis of a comprehensive Checklist which consists of the following categories:
Profile
- General Information
- Physical Data Location Customer Data
- Service Management
- Extended Company Profile
- Reference Information about the Cloud Service
- Certifications
Contract and compliance
- Adequate contract terms
- Rules for Data Management
- Contractual Data Privacy requirements
- Service Level Agreements
- Terms in case of bankrupt
- Terms for pricing and cost allocation
Security and Data Privacy
Operations and infrastructure
- General DC assessment
- Access control
- Area and environment assessment
- Resilience
- DC Operations
Operations processes
- Customer Support
- Service Management
- Data backup processes
- Quality assurance
Service Type specific assessment
- IaaS
- PaaS
- SaaS
Find out more about the Catalogue in the menu:
PUBLICATIONS
Data protection
Meeting national data protection requirements is a continual challenge for companies that process and store personal data in digital form on IT systems.
The term “personal data” covers all information about a person‘s private, professional or public life. Such data may include for example the name, a photograph, an E-Mail address, banking details, postings on the web pages of social media, medical data or the IP address of a computer. According to the Charter of Fundamental Rights of the European Union, everyone has the right to have their personal data protected in every sector of their life – at home, at work, when making purchases, at the doctor’s, in contact with the police and on the Internet.
When services are provided by a third party, highly transparent documentation is therefore needed of whom may process such information, in what form and in what amounts it may be processed and how protection of the personal rights of the individuals whose data is being processed can be guaranteed.
Data security
The concept of data security can be divided into two main categories:
- the functional security of the data in terms of confidentiality, integrity and ease of handling (generally referred to simply as “security”);
- the technical security of the system against malfunction, loss of data and other events tending to hinder proper data processing (generally referred to simply as “safety”).
In a wider sense, security may refer to IT security as a whole, covering the entire processing system and including hybrid use of one’s own IT facilities, private and public cloud services.
Technical security is often ensured with the aid of an ISMS (Information Security Management System), the quality of which can be certified for example on the basis of the ISO 27001 standard.
A widely used approach to the testing of functional security is COBIT (based on ESAE 3402, formerly SAS 70 II), which focuses on accounting standards, for example in connection with a company’s own balance sheet.
However, a qualitative statement of compliance with such standards can only be given after thorough examination of the assessment objectives and their application to the test requirements for cloud services.
Another field where thorough testing is increasingly required is that of cyber security. In an age where malware, DDoS (distributed denial of services), spyware and many other “viruses” are so prevalent, both the accessibility and the integrity of data is at high risk. This threat is not limited to the cloud, but affects all aspects of IT operation up to and including the devices used to access data.
Technical operation
The main requirements on cloud computing hardly differ from those on traditional IT outsourcing. Cloud services are provided from computer centres, where the usual physical security measures (site security, access control, network connectivity and security) and the necessary operability guarantees (on power, cooling and Internet connectivity) must be observed.
Processes and service delivery
All technical services obviously involve personnel, who have to receive the appropriate instructions and training in order to guarantee the provision of the services covered by the contract. The IT Infrastructure Library (ITIL) is a set of globally recognised best practices and test objectives in this field, which can be used to avoid problems and ensure proper provision of services.
The introduction of virtualization technology has blurred the traditional boundaries between networks, systems and software in this field. As a result, cloud service and infrastructure managers need to be keenly aware of their system responsibilities.
Interoperability
In most cases, only part of the relevant IT operations are moved to the cloud. It is therefore extremely important to check the availability of interfaces that permit movement of data in and out of the cloud, together, with the necessary applications and services.
A further very important aspect is the return of all data in a suitable form (machine-readable, and with preservation of the integrity of the logical data relationships).
Such interfaces and export facilities should also meet special security standards, since in some cases the service provider has fully automatic access to large volumes of the client’s data.
User support
General ergonomics and appropriate user guidance with self-explanatory Help systems and Hotline support are further required to ensure the acceptance of cloud services and their efficient introduction into companies. The user support may even extend as far as requirements for the abolition of all unnecessary barriers to the use of cloud services.
Quality levels
Three quality levels may be distinguished, depending on the test results obtained:
- Trusted Cloud Service – three stars
- Trusted Cloud Service Advanced – four stars
- Trusted Cloud Service Advanced HA (High Availability) – five stars

